Abstract
Based on the study of literature sources, the classification of security monitoring systems was studied, it was established which components such systems consist of, their relationship and functional purpose, and the advantages and disadvantages of frequently used security systems were determined. The reasons for choosing the Arduino platform are described, and the advantages over other programmable platforms are described. Based on tliis analysis, a wireless security monitoring system based on Arduino was developed for protected enterprises and organizations that have protected dispersed objects. The proposed wireless security monitoring system works on radio frequencies and Wi-Fi connection. Data transmission will be carried out on the frequency of 433, 920 MHz. This system is very flexible in terms of choosing different sensors. This is a block diagram of a wireless security monitoring system based on Arduino. Thanks to the presence of receivers and transmitters in the scheme, remote monitoring of the status of sensors of the protected object is carried out from a personal computer.
Introduction
Security services are now more relevant than ever before. If earlier security was more often required for offices and shops, and they accounted for the majority of orders, now more and more people want to protect their cottages and apartments from uninvited guests. Ensuring the security of dispersed objects from unauthorized entry and fire requires the development of rapid and automatic monitoring tools that are adequate to the current stage of information technology development. Therefore, the task of designing a centralized object monitoring system based on a wireless data network is relevant.
Research methods
In today, apartment burglar alarms are most effectively implemented using special monitoring systems.
Most often used for this purpose:
- panel protection;
- autonomous alarm system;
- wireless alarm system.
Any of these options can be executed independently, but it is preferable to use the services of professional security agencies. They can arrange the installation of a modern multifunctional sensors, alarms system and security video surveillance system.
Statistics show that a significant part of the robberies where material values are stored fall on private residences. Robberies usually prepare for this carefully and study place in detail, which they intend to enter. Sometimes the same house is stolen more than once, because new things are purchased instead of stolen ones.
Therefore, equipping housing with modern systems that ensure its safety is an urgent problem. Systems are constantly enhancing minimizing the likelihood of dodge guarding.
In order to ensure reliable security, a combination of trained personnel and technical equipment is required. For reliable protection of the protected object, a set of technical means is necessary to ensure the effective functioning of the alarm system.
Consider frequently used security systems:
- Panel protection. Security of objects using a centralized monitoring console or remote security has always been and is a relatively cheap way to ensure property security.
Let's consider the features of the remote control option for securing objects, and the factors that affect its effectiveness.
Advantages of panel protection:
- The owner of the protected object can not worry about its safety, knowing that the apartment or office is under the constant control of experienced security guards.
- If an alarm is triggered, assistance will be provided immediately. And the absence of the owner at the same time-not a hindrance.
- According to the terms of the contract with the security company, the owner of the dwelling receives compensation if the property was not secured. But, as a rule, security organizations value their reputation and prevent crimes in time.
Disadvantages of remote security:
- Security agencies set their own requirements for the owner of the property that is being protected (for example, residents of the first and second floors are usually required to put metal bars on the inside of the window). These requirements must be met.
- If a private house or cottage is taken under protection, the outer perimeter is not guarded.
- You must pay a monthly subscription fee, which may be increased over time.
- There may be unpleasant situations when false calls occur due to the fault of the owner, who does not comply with all the requirements of the security company. For example, sometimes the owner forgets to unguard a house or apartment. Some clients rent an apartment under security, leaving the window open, etc.;
- Security companies do not always undertake the protection of houses and cottages located in small towns or villages [1].
- Autonomous alarm system-а set of sensors and a control panel for disarming an object. It is usually equipped with a siren to deter thieves.
The benefits of autonomous alarm system:
- Creates a psychological barrier for the robberies.
- The system can be installed at sites where telephone communication or GSM- channel is not available (country cottages).etc.
- There is no need to pay a subscription fee to a security company (as happens in the case Ofinstalling remote security).
- There is a high probability of catching an attacker.
Disadvantages of autonomous alarm system:
- In situations of false positives, the owner may not always react quickly (he is at work or on vacation).
- After receiving an alarm signal, the owner must call the police, and this is a temporary head start for the robber. In addition, unfortunately, the outfit arrives more often too late than on time.
- All responsibility for the safety of property falls on the shoulders of the owner. The fact that there is an alarm system does not guarantee insurance payments if the robbery still occurs (except in cases when the object is insured against robbery and other types and causes of property damage) [2].
- Wireless alarm system. One type of wireless alarm system is GSM-alarm system. GSM alarm system is another modem and promising type of security alarm system. Such systems can be wired or wireless. GSM alarm system provides not only the alarm, but also notifies the owner by sms message or call to the mobile phone. GSM-alarm system can be used to protect various objects: apartments, cottages, warehouses, offices, etc. Thus, the alarm system will not only prevent entry into an apartment or other premises, but also provide prompt information to the owner.
Advantages of GSM signaling:
- Easy to install (it is quite possible to do it yourself);
- The system combines an excellent combination of reliability and low cost;
- Wide coverage area;
Large selection of models, the ability to choose the best option for any purpose, with the possibility of additional equipment;
- The alert function can cover about 10 phone numbers;
- Possibility to connect to the alarm system and control of electrical appliances;
- Ability to listen to remote objects;
- The human factor is excluded.
The main disadvantages of GSM signaling are:
You lose time between triggering alarm and your response to the signal;
When it works in a room with a low temperature faster battery discharge (for wireless systems) [3].
Research result
In this article, we propose to consider wireless signaling based on the Arduino platform. Arduino is an open programmable platform that consists of two main parts: a board (often called a microcontroller) and software for programming the board [4].
There are a lot of microcontrollers and platforms to create stand-alone interactive objects. Netmedia1S BX-24, Parallax Basic Stamp, MIT's Phidgets Handyboard, and many others offer similar functionality to Arduino. Arduino has a number of advantages over other platforms:
low cost - Arduino boards are relatively cheap compared to other platforms, in addition, the board can be done by yourself;
cross-platform-Arduino software is compatible with Windows, Macintosh OSX and Linux, most microcontrollers are limited to Windows [5].
The safety monitoring system on the basis of the Arduino will allow you to solve a number of shortcomings of other alarm systems. First of all, you don't need the Internet or cellular connection to transmit information. This system will use a wireless connection (Wi-Fi module and radio frequency transceiver). Data will be transmitted over a radio channel at 433, 920 MHz.
In addition, information is transmitted directly to the computer, which will allow constant monitoring of both the state of the security system itself and the state of the protected object. The proposed system will also be equipped with a fire-proof smoke detector, which will allow you to extinguish the fire before serious damage is caused, or quickly leave the room if it is already engulfed in flames.
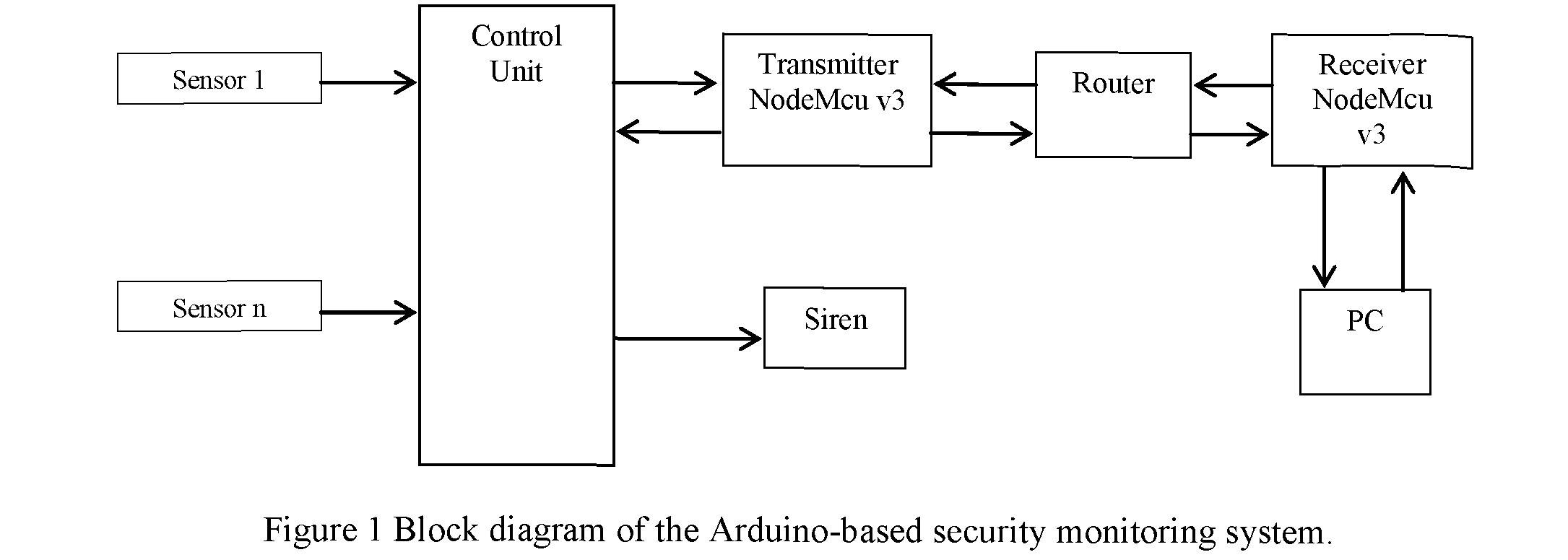
Figure 1 shows a block diagram of an Arduino-based security monitoring system.
Main components of the system:
- Senor 1 - Sensor n (pir sensors, intrusion sensors, smoke detectors);
- Control Unit - Arduino;
- Siren-Soundnotificationblock;
- Transmitter, receiver;
- The router - provides a wireless connection between the transceivers;
- PC- personal computer.
If any of the sensors is triggered, the control signal from the Control Unit output is sent to the siren.
Conclusion
Over all, information about the state of the protected object , due to the presence of receivers and transmitters in the scheme, is constantly sent to the PC, which allows monitoring at a distance.
References:
- Shutin A. Pultovaya ohrana na osnove setej sotovoj svyazi // Algoritmbezopasnosti. 2004, № 2, 44 p.
- Belkin V. Radiokanal sistemy peredachi izveshchenij // Algoritm bezopasnosti. 2004, .N 0 2, 26 p.
- Milman G. YA. Adresno-analogovye sistemy. Tekhnichcskoe obozrenie // Sistemy bezopasnosti. 2004, №2 (56). 64-65p.
- SommerU. Programmirovanie Inikrokontrollemyhplat ArduinoZFreeduino. - SPb.: BHV-Peterburg, 2012.-256 p.
 Evans V. Arduino Bloknotprogrammista - SPb.: BHV-Peterburg, 2015. - 357 p.
Evans V. Arduino Bloknotprogrammista - SPb.: BHV-Peterburg, 2015. - 357 p.